As the unrelenting surge of cyber incidents globally continues unabated, it is unsurprising that risk professionals across sectors have ranked cyber incidents as the top risk for the third consecutive Airmic survey. Disruptions to business operations, supply chains and critical services and infrastructure increasingly present significant and sustained risks to businesses across sectors, with almost 80% of respondents in the 2022 survey listing cyber security as a key systemic risk to their organisation.
These are long-running trends, but events in 2022 have also triggered rapid and significant changes in the cyber risk landscape for businesses, not least because of the Russia-Ukraine conflict. These changes – some likely temporary, others more permanent – have exacerbated the motivations and activities of threat actors, as well as worsening most organisations’ risk profiles around the world.
Although the sustained and disruptive nature of cyber risks more broadly is likely partly to blame for risk professionals’ increased concern, it likely also reflects growing unease over cyber threats and risks triggered by the situation in Ukraine. We have seen changes in the targeting intent and activity of actors across the spectrum since February 2022. This has ranged from state actors seeking intelligence on the conflict and the consequent sanctions regime, to a flurry of activity by cyber activists motivated by both pro-Ukraine and pro-Russia sentiment targeting organisations to support their respective causes. Cyber activists have increasingly taken geopolitical matters into their own hands, targeting Western companies that have remained in Russia since the start of the conflict, while other competing activist groups have launched retaliatory attacks against Russian and Western companies alike.
Meanwhile, ransomware and other cybercriminal threats remain unrelenting, with organisations across sectors facing persistent threats from such financially motivated threat actors. However, some cybercriminal threat actors have also adapted their operations and targeting as a result of the conflict and have increasingly focused their attention on organisations in countries perceived as adversaries to Russia.
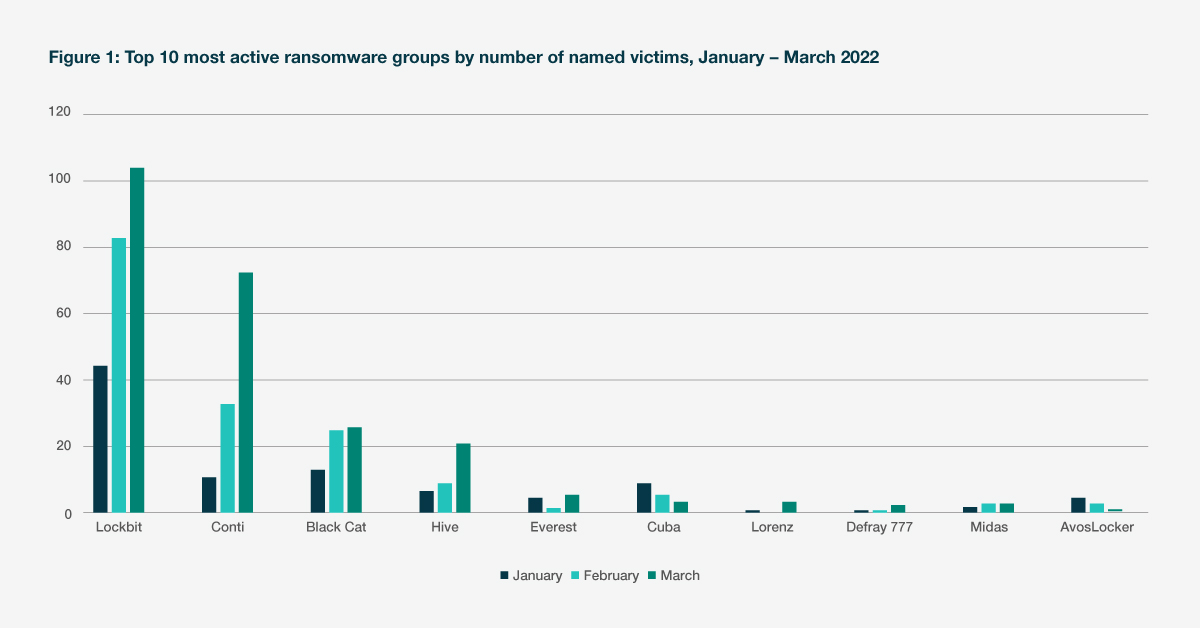
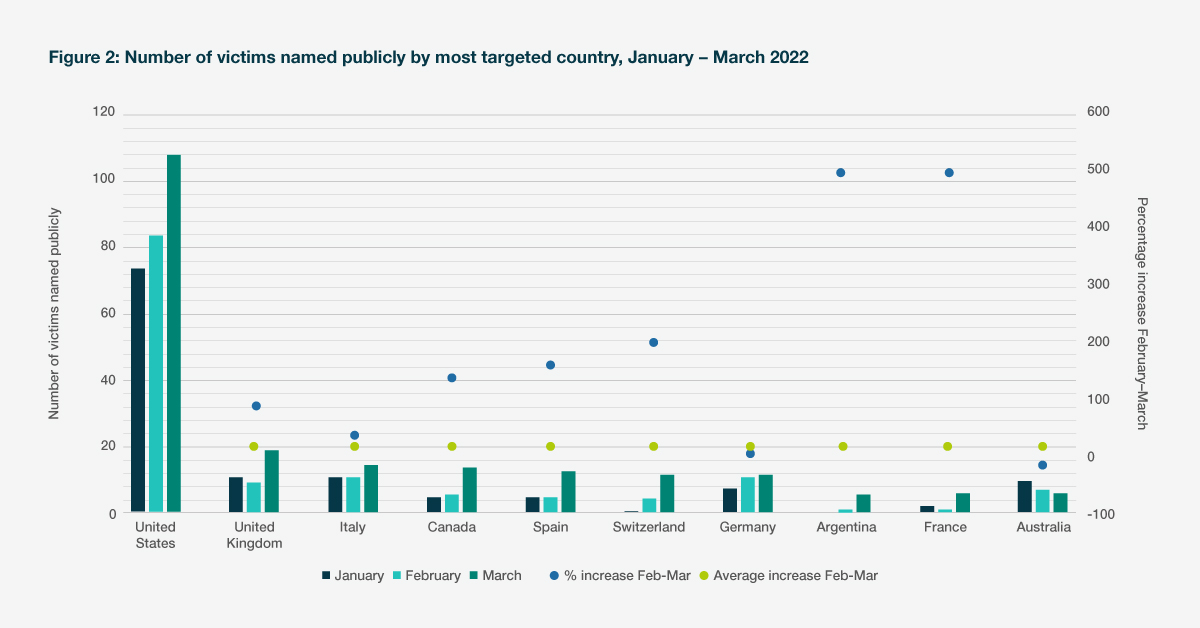
The Conti ransomware group provides the most explicit example. Shortly after the start of the conflict, the group announced its allegiance to Russia and declared it would target organisations and infrastructure in states perceived as adversaries to Russia. This resulted in the number of attacks by the group almost doubling between February and March, following the start of the conflict. Despite reports in May that the Conti group itself has ceased operations, the threat actors behind it are unlikely to disband and will almost certainly continue to pose a high threat to organisations across sectors. The conflict has broadened the geographical focus of some ransomware groups, which are now increasingly targeting organisations in jurisdictions perceived as leading the punitive response against Russia. The US, the UK, Canada, Spain, and Germany all experienced an uptick in ransomware incidents following the start of the conflict.
We have also observed an increase in targeting of critical national infrastructure and strategic sectors, such as attacks against oil and gas and renewable energy companies, with one incident leading to the shutdown of 17 oil port terminals in Europe. These disruptive attacks are increasingly targeted at supply chain companies, due to the cascading effects an attack against a physical or IT supply chain company can have on both the targeted organisation and its clients.
The conflict has also brought to the fore the sharp edge of offensive cyber tools through disruptive and destructive attacks targeting the Ukrainian government, defence, and critical national infrastructure organisations to aid military actions and objectives. Such attacks also increase the likelihood of spillover effects on supply chains and critical services beyond Ukraine, much like the 2017 NotPetya attack that led to unprecedented disruptions and costs globally.
As tensions persist, so too does the likelihood of retaliatory actions by a range of cyber threat actors, including disruptive distributed denial of service (DDoS) attacks and ransomware, posing additional challenges for risk professionals across industries. The developments in Ukraine demonstrate the growing impact of geopolitics on not just nation-state behaviour, but the broader cyber threat and risk landscape.
However, this is only one layer in an already crowded and increasingly complex cyber threat landscape, exacerbating the key challenges to organisations today. These trends are likely to persist. Cyber threat actors across the spectrum continue to target IT supply chains and third-party vendors to improve their chances of success, whether for espionage or financial gain. Such targeting increases the risks of operational downtime and data breaches for organisations relying on their services. As such, risk professionals not only need to consider direct and immediate threats to their business, but also the maturity and threat profile of their supply chains.
Internally, companies are now getting to grips with the fast-paced technological changes that Covid-19 brought to their business operations. However, the pace of technological change and innovation is unlikely to abate in the post-pandemic world, resulting in ever-expanding attack surfaces and new exposures for companies seeking to stay ahead of the curve. This growing interconnectivity – combined with an increasingly complex and entangled cyber threat landscape – will continue to underpin the systemic risks posed by cyber threats today.
Looking ahead, risk professionals need to understand the near- and long-term impacts of the conflict in Ukraine on the threats and risks to their organisations. They must also ensure that appropriate controls and measures are in place to mitigate those risks, while not losing sight of the relentless activities of cyber threat actors that challenge organisations every day.
However, to build truly secure and resilient organisations, it is equally important to learn from recent developments in the threat landscape. Understanding how real-world events can impact an organisation’s risk profile, irrespective of whether such developments are triggered by geopolitical rivalries or technological advancements, is fundamental to building an organisation that is prepared to face the next significant trigger of change in the cyber threat landscape.
About the full report:
The full report explores three key themes – cyber, ESG and people – and looks at how organisations can build resilience in a world where managing emerging risks and understanding systemic risks will be key. The report is based on 138 responses gathered in a survey conducted by Airmic from March to May 2022. Respondents hold leading positions within the risk profession and in some of the largest businesses in the world. Nearly three-quarters of them come from organisations with a global turnover of £1 billion to £10 billion or more, while almost 40% are from organisations with more than 25,000 employees.
Submit your details to download the full report:
