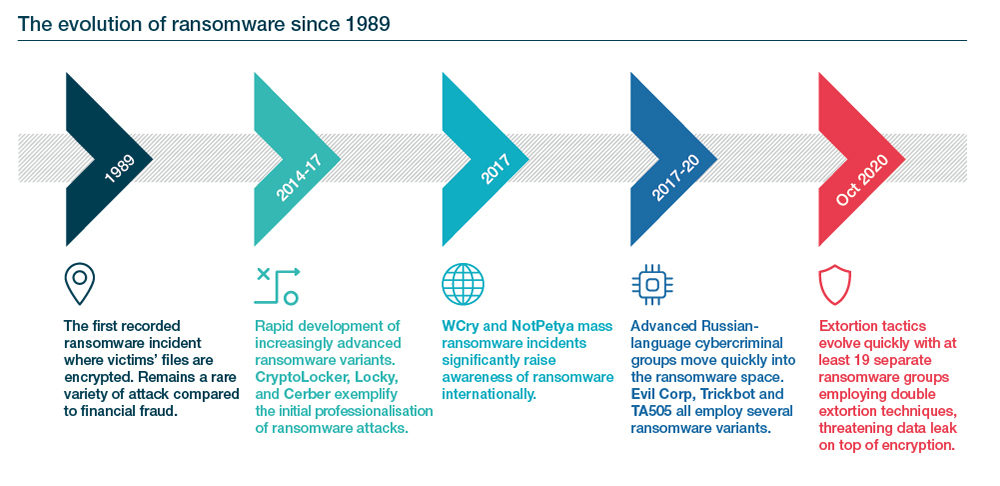
Ransomware extortion has rapidly become the key cyber threat to organisations globally. Organisations’ increasing reliance on digital services and interconnected business, IT and operational systems has led to rising profitability of cybercrime and ever more advanced cybercriminal tactics. In the past year, the COVID-19 pandemic has heightened such threats. This has encouraged advanced cybercriminal groups to deviate from traditional cybercrime and fraud in favour of ransomware extortion and is also driving less technically capable cybercriminals to adopt such methods.
The financial impact of ransomware on business can be crippling; some estimates place the total annual cost of attacks globally, including ransom payments and remediation costs, at approximately USD 170 billion. On a national level, the average cost of a single ransomware attack tells a similar story (see chart below). Operational downtime, out-of-hours and stretched resources, ransom payments, third party support and system rebuilds all make such incidents costly to remediate.
In 2020, many organisations witnessed first-hand the disruptive effects of ransomware incidents. One of the most cited examples was an attack in July against US-based multinational tech company Garmin, which not only encrypted the company’s files and systems, but also knocked its customer-facing apps, websites and call centres offline for several days.
Ransomware attacks can also carry increasingly significant real-world consequences. A German patient in September died after a hospital was forced to refuse her emergency treatment due to a ransomware attack on its systems. Although German law enforcement agencies found that the attack was not directly responsible for the patient’s death, further such cases are inevitable amid growing targeting of healthcare facilities.
Ransomware groups operate increasingly professionally
Some of the most prolific ransomware groups have begun to emulate business models, commoditising their ransomware tools and turning their criminal enterprises into franchises for other skilled cybercriminal specialists to buy into. They are also increasingly applying a wide variety of strategies to ensure maximum disruption to targeted organisations and their clients, which increases the likelihood that victims will pay ransoms. Such strategies include focusing on sectors most vulnerable to disruption (see Figure 3).
Several ransomware groups have also leveraged IT and communications organisations as pivot points into their clients’ networks. Groups such as Sodinokibi and NetWalker have disproportionately targeted IT and cloud service providers, leveraging reputational and regulatory risks by threatening to leak highly sensitive customer data to extort
higher ransoms.
Ransomware operators typically either conduct highly targeted attacks against a small number of high-value targets, or opportunistically target a broad range of networks to extort smaller but more numerous ransoms; some groups pursue both methods, or buy access to networks already compromised by other criminals. Beyond focusing on perceived high-value sectors, groups such as the now-defunct Maze Team and its successor Egregor have adopted a franchise model known as “ransomware as a service” (RaaS), in which less technically capable affiliates conduct attacks for a percentage of the proceeds, while more advanced ransomware developers provide the tools.
The growing adoption of the RaaS model increases the number of actors capable of undertaking ransomware operations, while increasing the impact such operations have on their victims. In the coming year, RaaS groups will continue to focus on recruiting highly skilled cybercriminals, with experience of breaching large corporate networks, into their operations. Multiple ransomware groups are also using innovative ways to monetise their victims’ stolen data, for example by auctioning it to the highest bidder.
State and criminal attacks overlap
The potential for financial gain from ransomware operations now extends beyond the cybercriminal ecosystem and has begun to attract state-linked actors, often referred to as advanced persistent threats (APTs). Examples include North Korean actors, who are widely considered responsible for the highly impactful WCry ransomware attack in May 2017, and who are now using a new strain called VHD to encrypt corporate networks of targets in Europe. Other actors, such as state-linked group APT41, will continue to use ransomware techniques to monetise access to the networks they compromise during espionage activity.
State actors will also continue to leverage relationships with cybercriminal actors to fulfil information requirements, obtaining stolen data that is relevant for states’ intelligence objectives. Such overlaps appear to be shaping the targeting patterns of cybercriminal groups that focus on targets in their host country’s adversary states; for example, a large proportion of attacks continue to target defence contractors, high-tech and government organisations in the US, the UK, and Northern Europe.
Alternative extortion techniques re-emerge
Encrypting, stealing, and threatening to leak data is no longer the only extortion method used by ransomware groups. Over the past five months, we have observed an increase in ransomware and other cybercriminal groups using alternative extortion techniques to coerce victims to pay. These range from extortive and disruptive distributed denial of service (DDoS) attacks, to extortive data-wiping attacks, to claims to have planted backdoors in software products, to auctioning or selling stolen data to the highest bidder. Ransomware groups can apply all of these techniques without the need to encrypt victims’ data.
The re-emergence of these alternative techniques demonstrates that cybercriminals are becoming increasingly aggressive in their extortive attacks. In 2021, we expect ransomware groups to continue exploring new and increasingly disruptive methods of extortion. This will almost certainly include the use of emerging technologies, such as deepfakes, which will further enable less skilled cybercriminals to extort businesses, executives, and individuals.
For cybercriminals, there remains a constant trade-off between profits and security against law enforcement and rival groups. For organisations, mitigation measures – built on proactive, threat-led cyber security solutions and well-rehearsed and realistic ransomware crisis scenarios – can prevent increasingly capable ransomware groups from forcing your business into a situation where a ransom payment is an enticing option.
