On 7 October 2023, the Palestinian militant group Hamas launched a surprise, multi-pronged terrorist attack by land, air and sea against military and civilian locations in the southern district of Israel. The Israel Defense Forces (IDF) have largely re-established control over southern Lebanon and prepares for an Israeli invasion of Gaza. These attacks have been accompanied by a series of disruptive cyber attacks from cyber activist groups targeting organisations in Israel and those perceived as pro-Israel in other countries. Cyber operations motivated by the conflict are likely to present a growing threat to organisations in the region, and potentially globally, as the conflict progresses.
What have we seen so far?
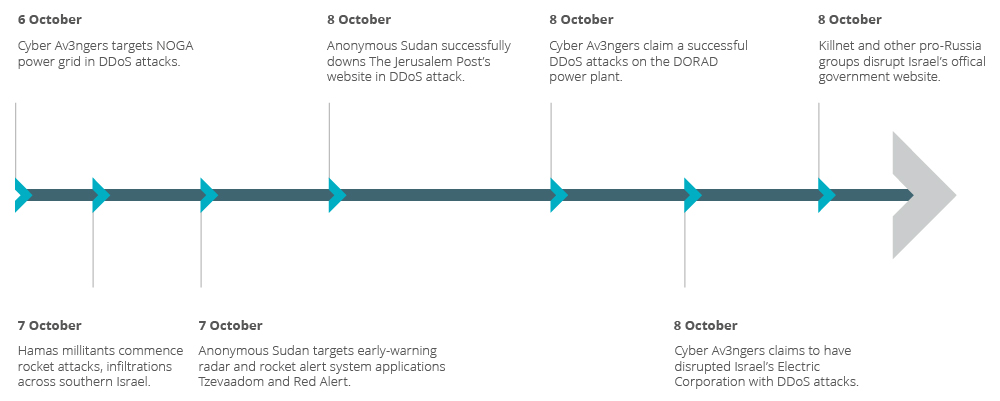
Cyber activists lead the charge: In the days since the conflict started, we have seen a sharp uptick in activity, primarily by cyber activist groups targeting Israeli organisations. More than 60 cyber activist groups have launched attacks against entities in Israel and the Palestinian Territories. These have mainly targeted critical national infrastructure (CNI) including government, communications and energy. Some groups have claimed attacks against Israel’s early warning radar and rocket alert system, power grid operator NOGA and the DORAD power plant.
Low-level capabilities dominating in initial attacks: Attacks so far have been limited to lower-capability tactics, techniques and procedures (TTPs) such as distributed denial of service (DDoS)1 attacks and website defacements, which have limited disruptive impact. However, the targeting choices, timing and swift engagement of both pro-Iran and pro-Russia cyber activist groups highlight a level of co-ordination in seeking to augment Hamas’ attacks and complicate the Israeli response. Pro-Palestinian activist groups globally have targeted Israeli government and media websites, with retaliatory attacks from pro-Israel actors against communications infrastructure in Gaza.
Israel to remain the primary focus; prolonged conflict likely to trigger wider targeting: Most targeting in the early days of the conflict has focused on organisations in Israel, and we expect this to continue in the coming days. However, activist groups such as the Ghost of Palestine have called on the global cyber activist community to attack targets in Israel and the US, highlighting the potential for spillover to other jurisdictions as the conflict progresses.
Figure 1: Timeline of significant cyber activist targeting, 6-8 October 2023
What are the threats?
Cyber activist threats to remain heightened: These initial attacks to augment Hamas’ operations and disrupt Israeli responses signal a high intent from pro-Palestinian cyber activist groups, as well as non-state and proxy groups aligned to pro-Russian and pro-Iranian objectives, to launch attacks in support of Hamas in the conflict. A prolonged conflict on the ground is highly likely to sustain a heightened threat to organisations from cyber activists aligning themselves with Israel or Hamas, with a short-term focus on targeting entities in Israel, including CNI and military targets. Cyber activists are likely to continue to employ typical lower-level capabilities including DDoS attacks, website defacements, doxing2, online shaming as well as disinformation.
Espionage threats to increase in the immediate term: Cyber activities are likely to closely follow developments in the conflict over the coming days and weeks. In the immediate term, we expect an increase in espionage operations on both sides to support operations on the ground, and pre-positioning3 to enable a forceful response as the conflict progresses. Israeli cyber threat actors are likely to step up intelligence gathering to identify and map funding, communications, key individuals and wider networks of Hamas and the Lebanese Shia Islamist movement Hizbullah to plan for disruption of adversary resources. This is likely to include targeting of regional and global banks, telecommunications, IT and technology companies.
Disruptive threats likely to expand as conflict progresses: A limited ground operation and Israeli siege of Gaza – Control Risks’ most likely scenario in the coming four weeks – is likely to heighten the threat from disruptive and destructive computer network attacks4 against military and civilian targets by more capable cyber threat actors. Such actors include Iranian state-aligned cybercriminal groups, who have demonstrated the capability to use disruptive tools such as ransomware and wiper malware against Israeli targets.
Conflict escalation likely to further heighten disruptive threats, likelihood of spillover: A fully unprecedented ground invasion with no restraint on use of force – our credible alternative scenario – would increase the likelihood of more disruptive attacks and likely motivate increased targeting by pro-Hamas activists against targets in Israel and beyond, particularly in the US.
Although we assess it as unlikely at this stage, a multi-front regional conflict that includes direct involvement of Iran and other regional actors would significantly increase the threats from highly disruptive campaigns by advanced persistent threat (APT)5 groups and proxy actors targeting organisations in the region, as well as key allies on both sides.
Prolonged conflict likely to trigger broader cyber activity in coming weeks: Based on observed activity during the Russia-Ukraine war by similar or the same groups, we expect to see an uptick in activity not directly focused on the conflict zone in the coming weeks. This is likely to include:
- Cyber activist targeting of third-party organisations declaring support for or perceived as supporting either side of the conflict, through DDoS and web defacement as well as doxing and disinformation.
- Heightened social engineering6 with threat actors mimicking aid organisations, news outlets and generally leveraging conflict developments as lures.
- Cybercriminal activity by Iran-based proxy groups targeting organisations in Israel or jurisdictions seen as supporting Israel, aligned to previous activity observed by such groups and Iran’s use of proxy actors to launch disruptive attacks.
What should organisations do?
Organisations with operations or third parties in Israel are likely to face heightened cyber threats from state-linked and cyber activist actors in the coming days and weeks. While we assess that cyber activities are likely to remain largely focused on the conflict zone in the immediate term, organisations beyond Israel and the Palestinian Territories perceived as providing support to adversaries’ battlefield or governmental efforts in the wider region and the US are likely to be prioritised for targeting as the conflict progresses.
Organisations should continue to closely follow cyber activity related to the conflict, monitoring key triggers for escalation as well as changes in targeting sectors and jurisdictions and tactics employed by threat actors.
In the immediate term, organisations with operations or third parties in Israel should:
- Employ traffic/packet inspection and monitoring, in particular measuring traffic volumes and defining a threshold of capacity alerting in intrusion detection systems (IDS) to help identify a DDoS attack in its early stages.
- Take extra care to monitor inbound traffic and logs surrounding local operations to identify potential compromises and intrusions.
- Ensure network detection systems are updated with relevant TTPs from threat actors known to target Israel for espionage, pre-positioning and disruption, including both state-sponsored and non-state proxy groups.
- Ensure incident and crisis management plans, including contact details for key staff and third parties, are updated and available to relevant team members.
- Prepare crisis management teams, designating crisis team members based on expertise across security, technology, communications, legal and business continuity and ensuring that key stakeholders are prepared for direct attacks against the organisation.
- Ensure that software, hardware packages and security software are patched and up to date.
- Test backup procedures to ensure critical data, systems and services can be rapidly restored if systems are disrupted or encrypted.
- For organisations running operational technology (OT)7 systems, ensure that manual controls for automated systems are fully functioning and that staff members are prepared to revert to manual processes if OT systems are disrupted.
Control Risks’ cyber experts are available to provide intelligence on strategic and tactical developments in the cyber threat landscape as the conflict progresses, to enable your organisation to proactively respond to evolving threats. We can support your planning and response efforts by ensuring crisis response plans and playbooks are up to date, that key stakeholders are clear on their roles, and that incident management teams are well-informed of threat actors’ evolving operations and tactics.
If you experience a cyber incident and require assistance, call our 24/7 hotline: +44 (0)203 356 2115
1 Distributed denial of service (DDoS) attacks aim to disrupt websites and network systems and prevent legitimate users from accessing them by flooding them with data requests.
2 The practice of publishing an individual's personal details – often including real name, address and phone number – online, usually with malicious intent. The information is gathered from open, freely available sources but often made to look like closed or classified information.
3 The preparatory compromise of computer systems, important to critical national infrastructure, with malware that can be commanded to disrupt or destroy such systems at times of escalation or when other strategic value can be gained.
4 A network intrusion, conducted by a state group or state-linked proxy, intended to disrupt, degrade or destroy the target network.
5 Advanced persistent threat (APT) usually refers to a nation-state group that has both the capability and the intent to persistently and effectively target a specific entity.
6 Manipulating victims into performing actions or disclosing confidential information that can be used to access computer networks to commit fraud or other criminal activities.
7 Hardware or software for controlling physical processes, including through direct monitoring of industrial or other physical devices or systems.
