Article for ICFP by Makoma Toona: Control Risks
Digital forensics is a branch of forensic science that deals with preservation, identification and analysis of evidence from digital devices such as computers, mobile devices, network and cloud infrastructure.
Traditionally, forensic evidence acquisition and preservation relied on the physical presence of experts at the client site to ensure that the scene is secured and relevant evidence sources are collected and acquired for analysis. However, in the last decade, remote evidence collection methods have become more prevalent and were a common practice among some experts even before the COVID-19 pandemic. The rise of the pandemic and ensuing travel restrictions have forced most digital forensics experts to adapt by rigorously accelerating their use of remote forensics to acquire and preserve evidence.
By the height of the pandemic, most organisations had established digital transformation strategies to aid in the transition of their businesses into hybrid working environments. This created a surge in cybersecurity vulnerabilities and cybercrime incidents, which required investigations assistance and remote evidence acquisition from digital forensic experts.
According to an INTERPOL report (2020), COVID-19 prompted significant shifts in cybercrime targeting, from individuals and small businesses to major corporations, governments and critical infrastructure. As organisations rapidly deployed remote systems and networks to support staff working from home, criminals exploited increased security vulnerabilities to steal data, generate profits and cause disruption.
To navigate the recent digital shift, Control Risks recommends that forensic experts use a baseline approach or methodology for collecting evidence remotely in support of a client, which can then be tailored to suit the client’s needs. To best determine a client’s needs during the scoping phase, forensics professionals should ask several key questions, a list of which we provide herein.
Approach and methodology
It is imperative that forensic practitioners plan for evidence collection and conduct thorough research based on various scoping elements before remote forensic collection. This will aid in establishing a bespoke approach to evidence collection for each client based on the scope of work. A baseline remote acquisition methodology should include the following elements:
1. Electronic evidence assessment
This process requires an understanding of device inventory and specification gathering.
2. Collection and execuition
This process includes the preparation and deployment of collection tookits and coordination with the client and custodians.
3. Verification
The verification of evidence transferred to the experts facility is crucial in verifying the completeness and integrity of data. This includes the collection logs, chain of custody documents and the evidence output (for example, the forensic image). At this stage, factors such as security mechanisms (encryption and passwords) may be established and mitigated.
Key considerations
During the scoping and planning phases of the engagements, it is important to consider the following questions:
- Are there any laws in the jurisdiction/s that restrict evidence collection?
- What is the IT landscape of the organisation?
- For what type of investigation is the evidence being collected?
- Has chain of custody documentation been considered?
- Are there potential risk assessments to be considered?
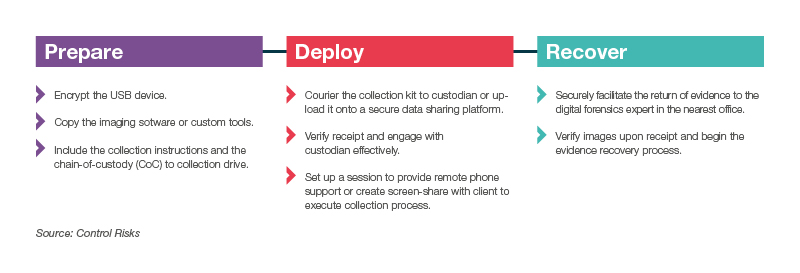
Below depicts a remote collection workflow that forensics professionals can follow when sending a collection kit to a client or custodian:
Challenges and advantages of remote evidence collection
Personal safety and the desire to limit the spread of COVID-19 was undoubtedly the largest factor motivating forensic practitioners to devise methods for remote collections. The subsequent advantages included cost-savings on flights, accommodation and other travel expenses, though challenges also arose due to technical issues, complications between jurisdictions and the availability of resources to assist in conducting a successful acquisition.
It is imperative that all parties involved in an investigation prepare accordingly and have a clear mandate and understanding of their role in the process. Some common pitfalls include:
- Delays – Delays should be factored into the investigation planning. Some jurisdictions’ customs authorities may hold hard drives indefinitely pending required documentation, such as destination address and receipient details, content description and monetory value of the items.
- Connectivity issue – Consider the physical location of the evidence sources and connectivity signal stength where possible, as these are essential to remote collection. Other interruptions, such as the loadshedding schedule in South Africa for example, should be considered in order to prevent disruption.
- Encryption and lack of passwords – The remote acquisition methods can be conducted in both an offline and online state. Encryption of system bios and a lack of credentials may pose restrictions in some instances.
During remote collections, the sources of evidence are not physically handled by the practitioner and therefore the traditional modes of securing the scene are impossible during remote collections. Digital forensic experts must rely heavily on the custodian assisting with the process to take proper photographs of the devices, assist in checking the system settings and other pre-acquisition steps.
Preservation techniques from various sources
Digital forensics has evolved from the days where personal computers were the primary source of evidence. At present, there are a multitude of sources to consider, such as mobile devices, as well as cloud and network infrastructure.
A forensic imaging toolkit that contains relevant software is usually prepared and copied to securely encrypted drives that are subsequently shared with the client. Evidence sources often include:
1. Computers
Prioritise consideration of encryption usage and encryption type. It is important for the toolkit to contain remote access software that will allow a viewer/forensic experts to access and easily navigate the evidence source. If remote access cannot be established, the practitioner should perform a walkthrough of the process with the custodian over the phone.
2. Mobile devices
The need for dedicated forensic tools to collect evidence from mobile devices prompted Control Risks to develop a virtual machine (VM) loaded with relevant mobile forensic acquisition software, which we send to the client using a secure data-sharing platform or physically via courier. Upon receipt, the practitioner is granted remote access to perform acquisition or similarly, a communication channel to complete the acquisition process.
3. Cloud
In response to the pandemic, Control Risks has expanded its remote forensic solutions. For example, Relativity Collect (a remote acquisition application) was used to acquire electronic information such as Microsoft 365 (“M365”) emails, calendars, contact and One Drive files, and to directly process that information in the Relativity eDiscovery platform. Leveraging cloud extraction tools was important during the pandemic to ensure efficient results in cases where forensic practitioners had limitations. Business email compromise cases presented many evidence sources and collections from cloud platforms, such as M365 audit logs.
4. Network infrastructure
According to an article by INFOSEC institute (2021), depending on the type of cyber-attack being investigated, a complex network may have several places from which evidence can be collected. Collaboration with client IT teams is imperative to scope and map out the data landscape for relevant collection.
Case studies
Control Risks has worked on numerous engagements that required remote collections. Our digital forensics experts were able to collaborate with IT teams from our clients to respond efficiently.
A. Ransomware Investigation Remote Collection (During COVID-19)
| Case Study | ||
|
The client A UK based entity |
The situation A ransomware attack affected the entire company, including virtual servers and workstations. |
Outcome We identified the root cause of the breach for the client and determined whether data was exfiltrated. With the information we provided, the client’s external legal counsel was able to identify information containing Personal Identifiable Information (PII) |
| Our approach
Control Risks identified the company’s key systems and network devices, conducted remote data collection and provided custom built tools. We monitored screen share sessions and logged extractions from firewalls and other network devices. We then collected and verified the data to transfer it through Secure File Transfer Protocol (SFTP). |
Remote considerations
The client assisted with remote collection from servers and firewalls. Over two terabytes of data was collected over a two-week period. |
|
The future of forensic evidence preservation
COVID-19 has catapulted remote digital evidence recovery as the most preferred style of collection due to its efficiency and cost-saving benefits, but the current technology is unlikely to be able to cope with the large data volumes expected in future acquisitions. In the coming years, this and other forensic evidence preservation challenges will be solved with emerging technologies, such as AI, which will automate certain acquisition processes. AI, like COVID-19, will once again change the way forensic professionals use technology to conduct their work.
