While threat actors’ technical capabilities grow, traditional use of phishing remains a powerful tool for exploiting what is often an organisation’s greatest vulnerability – their people. Although basic spam campaigns will continue to target indiscriminately, threat actors are changing their tactics to target more mature organisations.
Changes in working practices including remote working and a shift to cloud solutions, as well as geopolitical rifts and a looming economic downturn, have created the perfect conditions in which phishing is more likely to succeed in bypassing technical controls. Phishing rates and social engineering capabilities are rising at a time when organisations are still working out what a good hybrid security posture looks like and how best to maintain it.
More targeted, harder to detect
Sophisticated threat actors are updating their tactics and messaging to overcome employee assumptions about what phishing involves. Phishing messages often contain an urgent call to action to convince victims to act without thinking twice; however, we are now seeing threat actors removing the urgency to avoid raising victims’ suspicions.
Recently we have reported on Iran-based threat actors employing multiple personas in the same email conversation. A second or third persona can validate the credentials of the first, making any call to action less suspicious. The threat actors can therefore delay sending a malicious link or attachment until they have earned the trust of their victims.
We have also reported on threat actors using hybrid phishing tactics, such as sending an email to their victims and encouraging them to call a telephone number. Over the phone, threat actors can use further social engineering to convince their victims to divulge sensitive information or grant access to their system by installing remote desktop tools. The combination of email and telephone phishing reduces the predictability of attacks by allowing them to vary, making them more difficult to counter.
As well as generating trust, threat actors continue to develop lures that play on their victims’ fear and concerns, including about recent events. During the last three years, we have seen lures evolve and proliferate in relation to COVID-19, vaccination campaigns and the conflict in Ukraine.
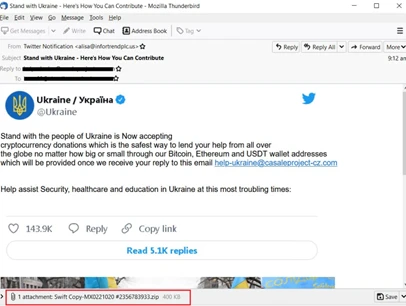
Figure 1: An example phishing email leveraging the Ukraine conflict to hook users into making virtual currency donations
www.trendmicro.com/en_dk/research/22/c/cyberattacks-are-prominent-in-the-russia-ukraine-conflict
As energy prices have risen, the UK’s fraud and cybercrime reporting centre has in recent months warned that threat actors were posing as the UK government and contacting members of the public with energy bill rebate scams. Similar phishing messages have been reported in Germany. Meanwhile, the US’s Internal Revenue Service (IRS) in September warned taxpayers of an “exponential” increase in smishing messages, which are carried out over SMS messaging rather than email, requesting personal and financial information from taxpayers. In the months ahead, expect a sharp rise in phishing campaigns that play on victims’ concerns about energy bills and the state of their personal finances. Threat actors particularly those based in North Korea have long used lucrative fake job offers in phishing campaigns. With inflation delivering real-terms pay cuts, victims are likely to be increasingly more receptive.
Know your adversary
Phishing is both a key tactical threat to your organisation but also an incredibly rich intelligence source to identify who is targeting your employees, which employees are being targeted and how threat actors are doing this. It is now vital to leverage a combined human, technological approach to counter-phishing in using endpoint protection and counter-phishing technologies to identify and block phishing campaigns, while using the data received from these technologies to better understand your company’s specific threat landscape. Security teams should still drive forward frequent corporate education campaigns but these should leverage the team’s understanding of the social engineering campaigns your staff are facing with training, awareness and education tailored to key user groups and threats.
Understanding the adversaries targeting your network will also help you identify where actors are attempting to bypass your technologies with high-sophistication attacks. Knowing who is likely to do this will ensure you are able to build additional controls and hold third party providers to account.
