The technology landscape in Africa is set to evolve rapidly in the coming years with several factors combining to set the scene for an impending technology boom. The technology market in Africa is predicted to grow sevenfold by 2050, with Africa’s large population of young people (one third of the world’s under-18 population), its growing internet user base (predicted that one sixth of global internet users will be based in Africa by 2025) and one of the quickest-growing startup markets globally, with investment rates for digital startups two times higher in Africa than the global average in 2021.
Africa’s technology boom is happening at a time of global technology revolution. Most critically for the convergence of physical and cyber risks, the number of manufacturing, security, transport, and physical systems that are internet connected is increasing exponentially and the number of “things” (such as vehicles, shipping, and manufacturing systems) connected to the internet has overtaken the number of mobile devices, laptops, and traditional IT devices. This sets the scene for a greatly increased physical risk and impact emanating from these devices and the physical and operational systems they connected to.
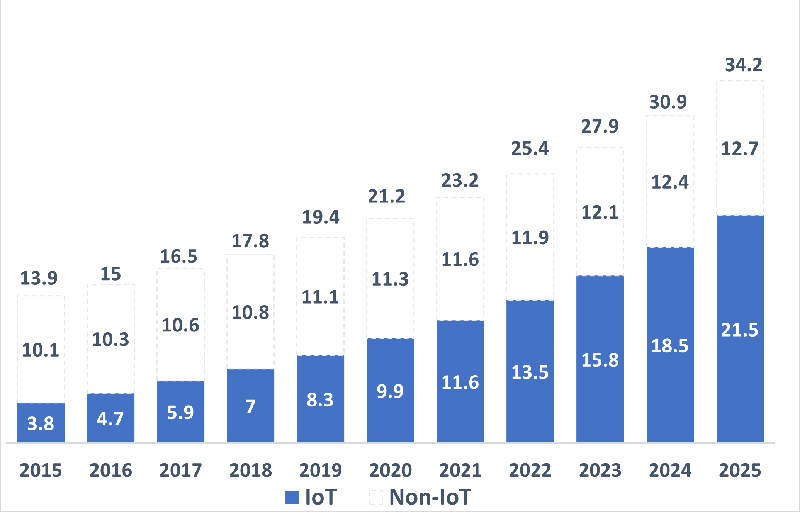
Figure 1: Total number of active IoT and non-IoT connections (bn)
Mature and effective cybersecurity will also be fundamental to technology success in a region where cybersecurity standards and resilience at the state level falls behind leading countries in Europe, APAC and North America. While African nations are relatively developed in implementing legislation and regulations around cyber security resilience and in incident response, the region lacks systemic investment in capacity development, the strong organisational foundations needed at the state level to deter threats (e.g. cyber incident response teams – CIRTs) and the technical measures to prevent and counter cyber security threats, putting the burden on enterprise to ensure good organisational-level security and resilience.
Geopolitical competition and the evolving global cyber threat landscape converge to create challenging digital risk landscape.
Geopolitical competition in Africa has moved beyond diplomatic, military, or commercial influence into the cyber sphere, with competition now playing out online in many countries. For instance, in the Central African Republic (CAR), what began as opportunistic diplomatic engagement by Russia – which exploited Western countries’ refusal to provide weapons to the country’s armed forces under an embargo – has expanded into wider Russian influence in the political and business environment and ultimately into the media and internet landscape, which have been targeted by pro-Russian and anti-French mis- and disinformation campaigns. Similar information operations have been carried out in Sahelian countries such as Mali and Burkina Faso, where Russia has increased its influence in recent years at the expense of historically influential and recent counter-terrorism partner France. The Russia example above demonstrates that leading cyber capable state actors will increasingly leverage their own cyber capabilities to influence favourable outcomes in African domestic and geopolitics, while facilitating cyber capability development for allies in the region.
Ransomware on the rise in Africa
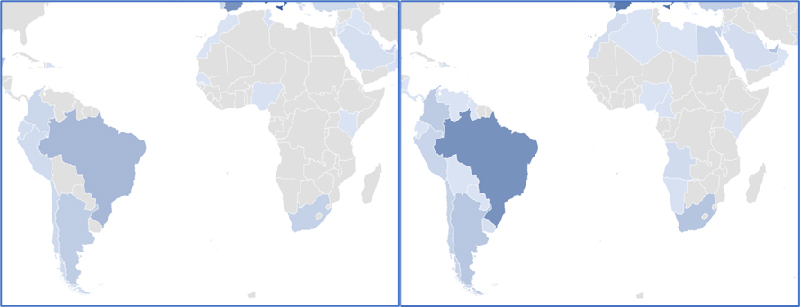
Ransomware has long plagued companies and organisations globally, disrupting critical systems, leading to operational disruption, and leading to large amounts of data being stolen and leaked online. Ransomware incident volumes are at their highest ever levels and groups continue to turn the dial on the cyber security landscape by rapidly improving their capabilities, disruptive tactics and revenue generating strategies. Figure 3 compares the proportion of ransomware incidents per country in the Africa and LatAm continents in H1 2022/2023. The map shows consistent increase in the proportion of incidents and the number of countries targeted in these two developing continents.
Case study: Transnet ransomware disrupts key container terminals.
Background: The Five Hands ransomware group in July 2021 successfully targeted and disrupted Transnet operations in South Africa, leading to disruption of container movement operations in Durban, Ngqura, Port Elizabeth and Cape Town. The Five Hands group is an aggressive criminal group, likely originating from Russia or Eastern Europe, that aims to disrupt systems and steal data to receive ransom payments from its victims.
Impact: The cyber incident targeting Transnet impacted physical port and container operations, leading to Transnet declaring force majeure in relation to existing contracts due to the significance of the incident. Transnet needed to return to manual systems for a period of time before business-as-usual operations were returned to normal.
These agile criminal groups are also learning quickly that there is a growing “marketplace” to generate criminal revenue in Africa with an increase in the number of incidents targeting African countries year on year, with North African states and South Africa facing the brunt of incidents. This threat will continue to grow as technology growth continues in the region, while security lags behind.
Figure 2: Global number of named ransomware victims (January 2021 - June 2023)
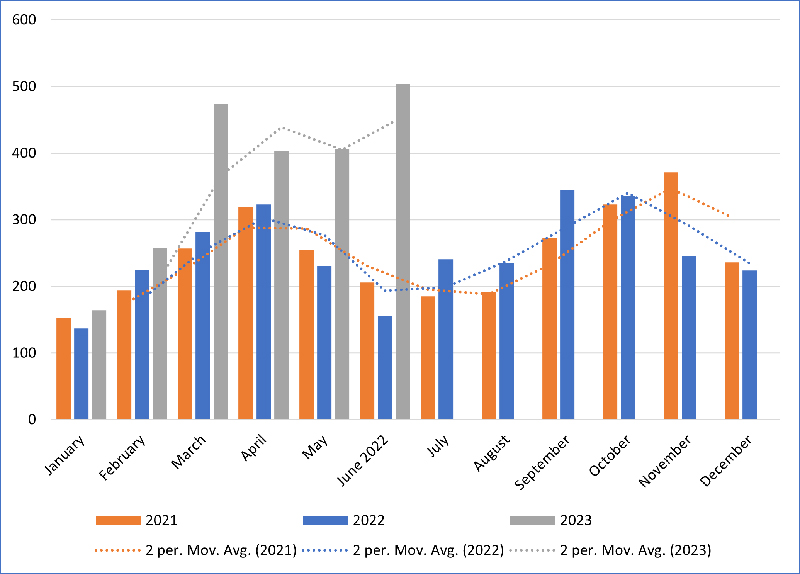
Figure 3: Proportion of ransomware victims globally in Africa and LatAm versus global victims (left, H1 2022; right, H1 2023)
Outlook for Africa
These issues are likely to become increasingly relevant across Africa as the cybersecurity threat landscape becomes more sophisticated in the coming years. Both businesses operating in Africa and African companies looking to expand outside the continent will increasingly need to consider cybersecurity alongside physical security in their planning. The former are likely to face increasingly sophisticated cybersecurity threats and growing exposure to physical issues – such as geopolitical competition or criminal activity – becoming more prominent in cyberspace. These effects are most likely to play out in strategic sectors, where geopolitical competition is more intense. One notable example is in mining, where need for critical minerals and competition over sourcing them will continue to intensify. In the coming years, cyber threats in Africa could become a key source of threat and disruption to businesses, necessitating greater planning and preparedness, similar to how organisations manage security threats from crime, militancy or community disputes today. Meanwhile, many businesses operating in Africa have been spared the spillover of threats from conflicts elsewhere – such as in Ukraine – into cyberspace; but they will need to stay ahead of the curve as they face a wide variety of new threats when expanding into new regions.
Mitigation strategies
Mitigating such significant digital risks in the region will require more than just technology-based controls. A hybrid approach should be taken where both physical and digital risks are considered and addressed in tandem. When considering measures that threat actors may utilise to breach physical security, organisations should be aware that attackers increasingly exploit vulnerabilities in online security to gain data useful in targeting a victim. There is a correlation between cyber security vulnerabilities and physical security risk.
In the simplest sense, strong physical security measures around critical IT and cyber infrastructure are essential to the ongoing security of those systems. By preventing intrusion and by building accountability into methods of access, these cyber assets have the integrity of their security assured. Physical and cyber security should always be aligned. Physical measures such as perimeters, surveillance and detection systems, lighting, and access control, along with manned guarding, all work to protect infrastructure that hosts digital assets.
The way that security professionals approach their assessment and mitigation of cyber security threat and risk can be based on the same methodology traditionally used in the physical security space. An initial assessment of the threats that could seek to do harm to an individual or organisation should be the base for any assessment. However, instead of examining the risks of thieves or attackers, consideration is given to the online presence of hackers or malware. Having assessed the threats, a gross assessment can be made of the likelihood of each threat manifesting and of the impact were it to do so. Having assessed the likelihood and the impact of each threat occurring, the risk can be understood. Mitigation measures can then be planned to better protect cyber systems via the same methodology as a physical security professional would apply. A re-assessment of the net likelihoods and impact will allow a risk manager to understand their cyber risk exposure with the same level of understanding as a physical security colleague would expect.
Beyond the risk assessment methods employed, organisations should also add more hybrid physical-digital approaches to a variety of resilience-related topics. For example, running cyber-focussed crisis management simulations for senior teams can be extremely valuable in highlighting how a cyber incident may result in an enterprise-wise crisis that can be existential. It also provides a safe space for non-technical executives to learn and engage with cyber as a topic while using a familiar crisis management approach they will have seen in previous non-technical crisis management exercises e.g., evacuations, terrorist attacks etc. Similar approaches should be considered in relation to other resilience and assurance activity such as disaster recovery and penetration testing.
