As the scale and frequency of cyber attacks continue to grow, the impacts of cyber security incidents on companies continue to escalate. Breaches of sensitive personal data, theft of intellectual property (IP) and sensitive business information, and disruptive ransomware and distributed denial of service (DDoS) attacks can adversely impact companies’ financial results, share value, brand and trust among customers and clients.
At the same time, companies and investors are increasingly required to disclose breaches to regulators, shareholders and customers, and stringent data protection rules under GDPR and similar frameworks are driving more decisive regulatory enforcement, including large fines and lawsuits from affected customers. As a result, limited cyber security and data protection policies, hasty technology implementation and poor crisis management planning are increasingly in the limelight following large-scale breaches.
Despite well-known incidents such as the Yahoo and Marriott breaches – which should have put cyber due diligence firmly on any investor’s agenda – a systematic and risk-based consideration of cyber security in the investment lifecycle is still the exception rather than the rule, elevating reputational risks for the investor.
The need for cyber due diligence extends across sectors
Rapid digital transformation – accelerated by the COVID-19 pandemic – and the ubiquity of technology across all sectors of the economy means cyber risks impact all companies, not just the most digitally advanced. In essence, all companies are now technology companies. Cyber threat actors know this and are acting on it, with some of the most impactful breaches in recent years affecting companies such as pipeline and infrastructure operators, food producers, healthcare and education facilities, among others. As a result, the need for thorough cyber due diligence is as relevant for private equity and infrastructure funds investing in other sectors as it is for technology-focused investors.
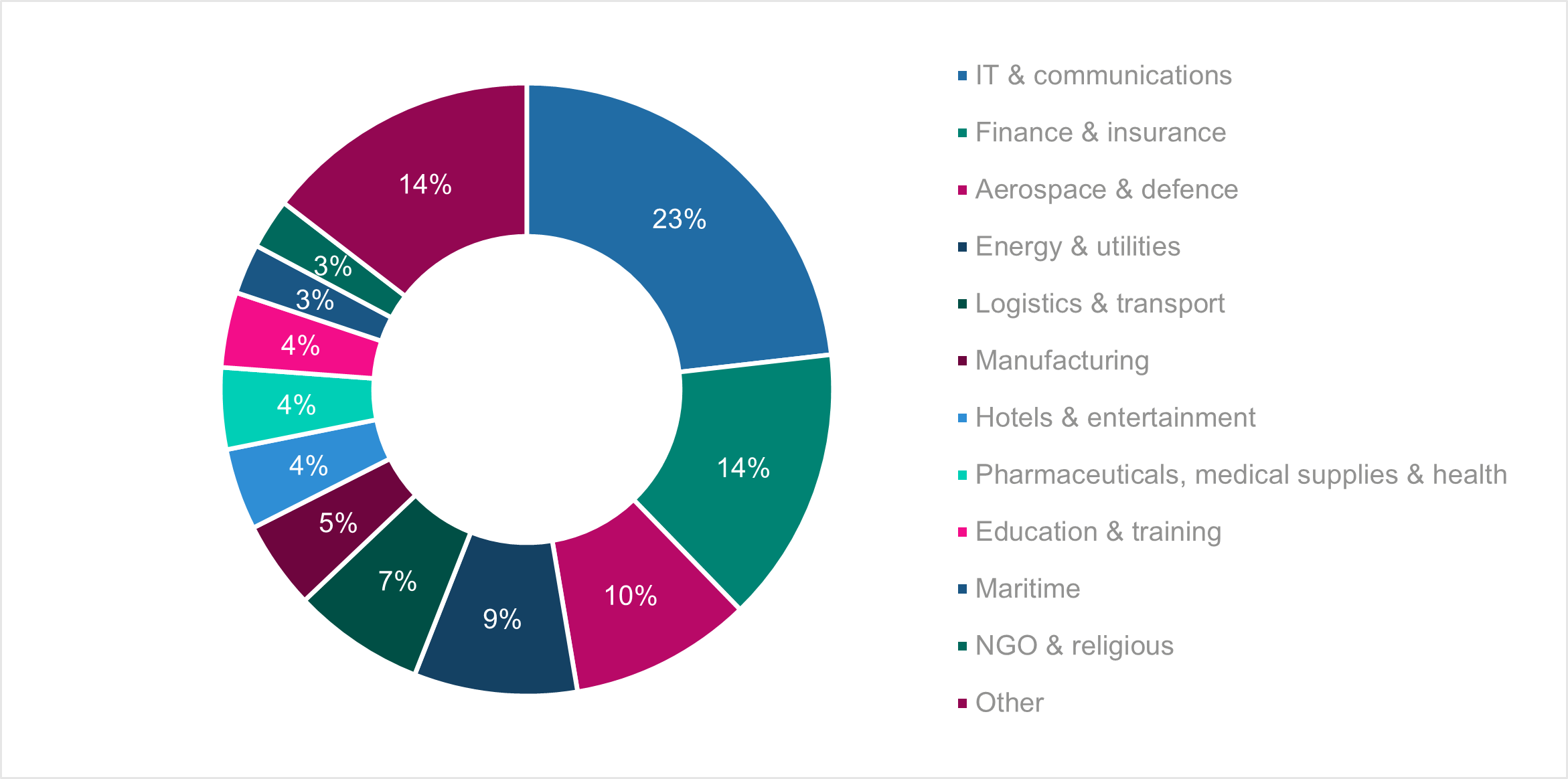
Figure 1: Most frequently targeted private sector organisations in cyber attacks globally, October 2021-November 2022
Finding this article useful?
Integrating cyber due diligence into the investment process
For investment teams unfamiliar with IT and cyber security, the concept of cyber due diligence can seem nebulous and difficult to grasp. However, cyber due diligence is not something fundamentally distinct and separate from other diligence processes; its basic purpose is to assess risks to the investment, ensure correct valuation and flag areas of further investigation or remediation. As a result, many familiar risk factors are also critical when conducting effective cyber due diligence:
Outside-in due diligence: assessing the external risk profile of a target acquisition
At the pre-investment stage, before investors have full access to the target acquisition, cyber due diligence can provide useful insight into a company’s exposure to cyber threats. Such an assessment will provide investors with a view on the external threat profile of the company by investigating factors including:
- its sector and geographic footprint
- the nature of its operations; for example, if it holds sensitive IP or large amounts of personal information
- critical third party and external relationships, such as clients and customers, that could increase its attractiveness as a target for cyber threat actors
- evidence of past breaches of the company and technical vulnerabilities in its IT infrastructure
A thorough assessment of the potential cyber risks of a target acquisition helps an investor understand the level of risk it is taking on, and the cost and timeline for remediation in the early stages of the investment process.
Inside-out due diligence: understanding internal cyber security governance and risk management
Once a prospective investor has access to the target, a more thorough review of a company’s internal cyber security governance can be undertaken. Reviewing policies and procedures and interviews with key stakeholders, alongside assessing its IT infrastructure and vulnerabilities, provides insights into internal cyber security maturity and current risk management processes.
This process is designed to identify potential risk factors such as gaps in current cyber security posture, or inadequate crisis management or business continuity procedures in the event of an attack. Understanding the internal cyber security maturity of a target acquisition also helps investors prioritise remediation efforts and develop effective post-acquisition integration plans.
Investment teams should consider cyber due diligence as another tool in the toolbox to make informed decisions, rather than something daunting and exceptional. The growing scope and impact of cyber attacks – coupled with increased regulatory and public scrutiny of companies’ cyber security practices – only affirms the need to systematically integrate cyber due diligence in the investment lifecycle.
Cyber due diligence helps manage risks throughout the investment lifecycle
As with other forms of transaction due diligence, cyber due diligence helps inform decision-making and negotiations before an investment. Control Risks’ insights into existing and future cyber security challenges, past incidents that could affect the value or brand and the potential cost of remediation have supported our clients to accurately value a target acquisition, inform contractual negotiations and prioritise remediation actions following the acquisition.
In a recent case, Control Risks supported a private equity firm seeking to invest in a software development company. Our client had concerns about how the target acquisition secures its source code. We outlined the infrastructure, systems, people and vulnerabilities that could be leveraged by a cyber threat actor and, on this basis, produced a threat rating for the third party and for each identified vulnerability. This was delivered alongside a reputational due diligence report to provide a comprehensive view of the target’s maturity across several areas. This allowed the client to reassess its valuation of the investment and build a post-investment cyber security strategy, using our ratings as a guide to prioritise effective remediation activity.
Cyber due diligence is also often used by our clients following a specific acquisition or as part of portfolio risk management. In that phase, cyber due diligence provides a prioritised view of the cyber security maturity of portfolio companies, to protect value and serve as a cyber “health check” on investments. Conducting thorough checks of the cyber hygiene throughout the investment lifecycle can help mitigate reputational, financial and legal risks if a breach occurs, as this often triggers scrutiny of what steps have been taken before or after a deal. In our experience, cyber due diligence is also a vital tool following a breach, to investigate an incident and then build back better.
In another example, a technology client approached Control Risks following the acquisition of a company operating a software-as-a-service model, with concerns regarding how it managed confidential case data and personally identifiable information (PII). We outlined the technical and process vulnerabilities that could be exploited, and the most prominent cyber threat actors looking to target them. This was based on a thorough document and process review, technical test, and a series of interviews. Through this assessment, the client was able to identify key remediation points, for example removing vulnerable legacy systems supporting client systems, introducing additional technology to improve perimeter security, and improving resilience procedures.
As cyber threats are here to stay, it will be critical for investment teams to systematically assess the cyber exposures associated with an investment, to protect value and mitigate reputational and regulatory risks. Leveraging cyber due diligence throughout the investment cycle – from pre-acquisition decision-making to post-acquisition portfolio management through to post-breach investigative and risk management support – can help investors stay ahead of the curve and protect both value and brand.
